This IDC article looks at identity management in reframing APAC cyber security as an opportunity for Asia/Pacific businesses to gain a distinct advantage, especially amid uncertain times.

In the face of the new normal CEOs’ new mandate in the digital economy: TRUST
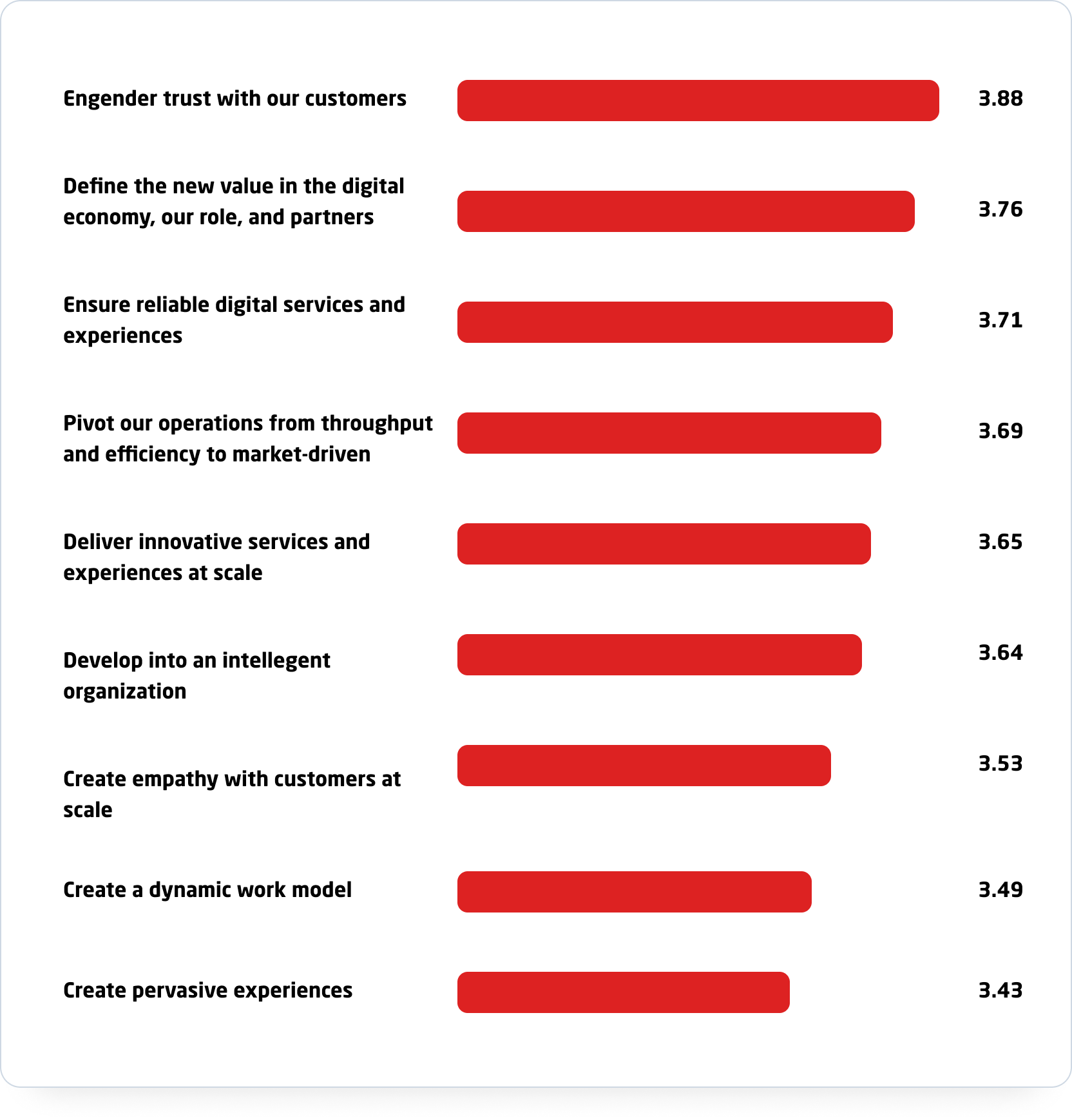
Engendering trust, defining new value, and ensuring reliable digital services and experiences rank highest in importance to the overall business vision. Respondents were asked to rank their strategic business priorities, with 1 being the least important and 5 being the most important.
Remote working as part of the future of work
Remote working is no longer a nice-to-have but a critical element of business resiliency and continuity plans, and for many, may become business as usual.
- 60% of Asia/Pacific employees surveyed want remote access, but only 40% have it.
- 40% of Asia/Pacific respondents in banking and financial services cited productivity gains due to remote access.
Key security challenges
Security resource issues
30% of Asia/Pacific organisations suffer from a lack of skills to ensure reliable and secure digital services. The talent shortage is more critical in Singapore, while Australia and New Zealand are in line with the regional average.
- Asia/Pacific average: 30%
- Singapore average: 55.6%
- Australia average: 33.2%
- New Zealand average: 33%
Insufficient security management focus:
- 10% of organizations have a dedicated chief information security officer (CSO or CISO).
- 80% of organisations assign the head of IT (CIO or IT director) as the head of security.
IAM headcount
Enterprises with at least 500+ employees surveyed by IDC have an average of 23 full-time employees in the IT security department, with more resources focused on IAM than any other area of IT security.
Percentage of time spent by security role:
- Identity management: 29.1%
- Threat management: 24.7%
- Trust management: 23.4%
- Vulnerable management: 22.8%
Considering the importance of threat identification, the ability to transfer valuable resources by improving IAM efficiencies would be considered a strategic move.
Looming identity crisis
Businesses are still warming up to MFA and federation for enhanced security.
- 23.4% of Asia/Pacific organisations plan to deploy MFA for all users accessing sensitive data.
- 30.4% of Asia/Pacific organisations are considering or piloting identity federation plans.
- 29.1% Disconcertingly, 29.1% surveyed are not even considering federation.
Remote working is here to stay
Business and IT leaders must address the security changes head on:
- Control over corporate network access from employees’ managed and unmanaged devices.
- Addressing the complexities of authentication and compliance.
- Adopting a strong cyber risk governance practice.

Building a trust agenda through trusted identities
Today’s boardroom agenda calls for a prioritisation on driving security, specifically identity.
Strategic investment in IAM is one way to address many of these issues, particularly where users and identities are validated and monitored.
Top 5 challenges for 2020–2021:
- Increasingly sophisticated external cyber threats: 37.9%
- Legacy IT architecture and technology: 32.4%
- Quantifying/measuring the business benefits of improving trust scores: 31.7%
- Increasing regulatory compliance requirements: 29.0%
- Significant support required for vendor partners ecosystem: 19.3%
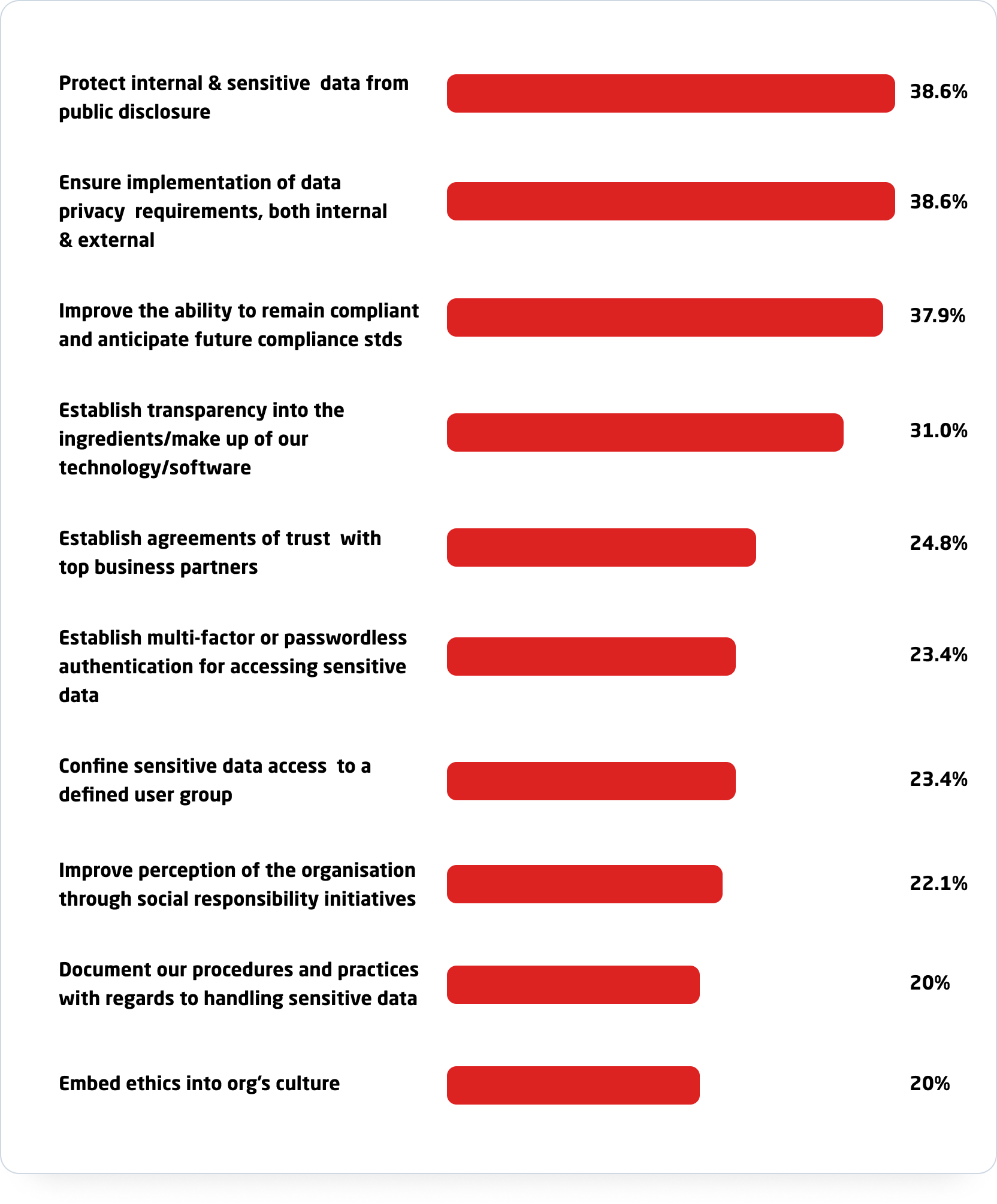
Future of trust: top goals for 2020-2021