-
Why LastPass
-
Pricing
-
Personal
-
Business
-
Partners
ALLEGIANCE PARTNER PROGRAM -
Support
-
Log In
-
Contact Sales
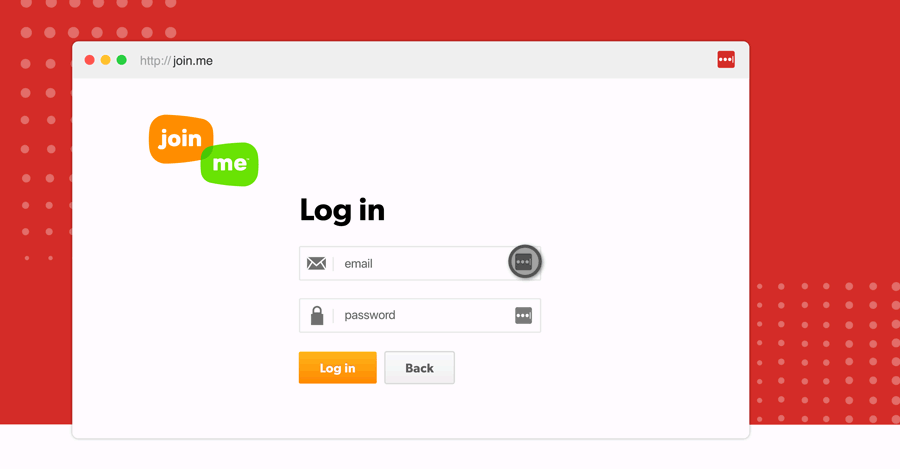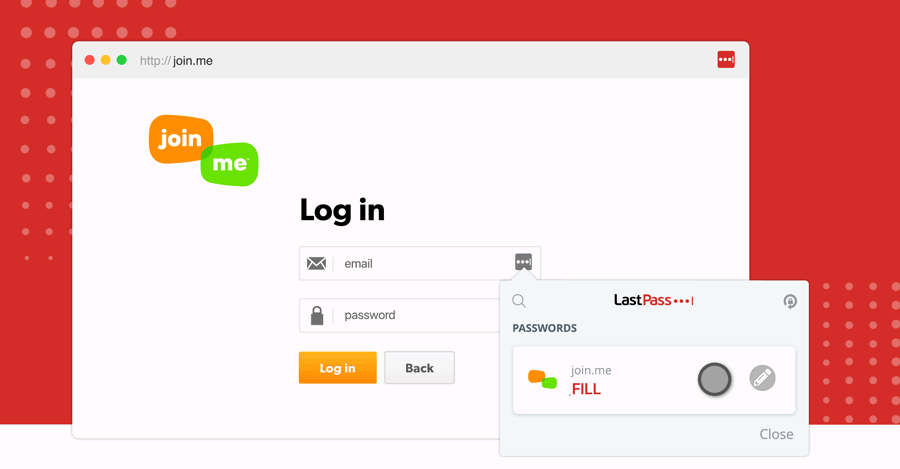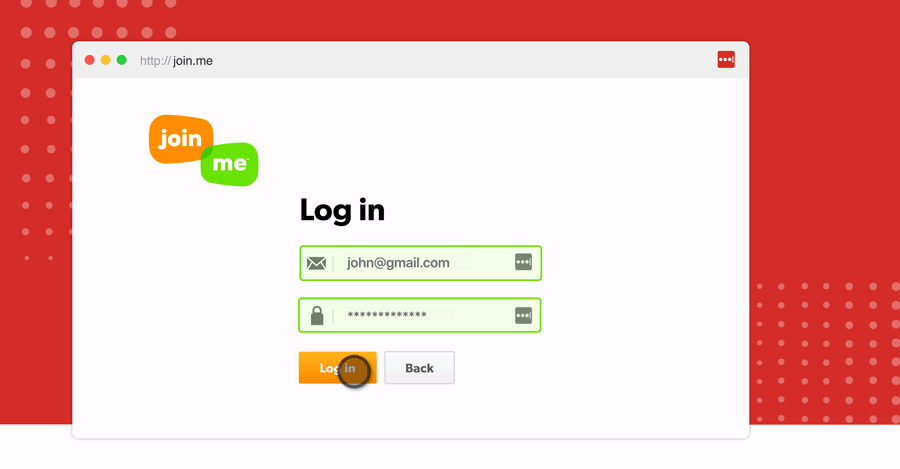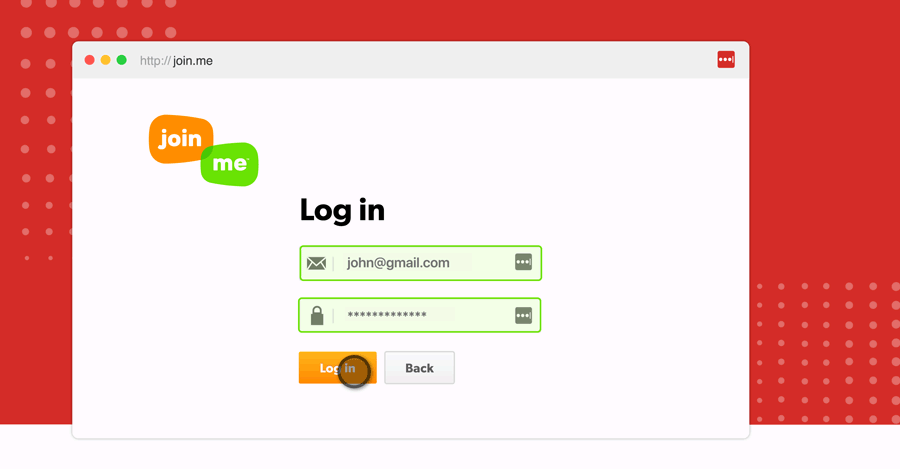
Log in through the extension
LastPass is best experienced through your browser extension. Install LastPass for Firefox to automatically login to sites as you browse the web.





























