Stay ahead of the curve with cybersecurity education
There are four critical pathways to your estate: Credentials, Phishing, Exploiting vulnerabilities, and Botnets.¹ All four are pervasive in all areas of the DBIR, and no organization is safe without a plan to handle each.
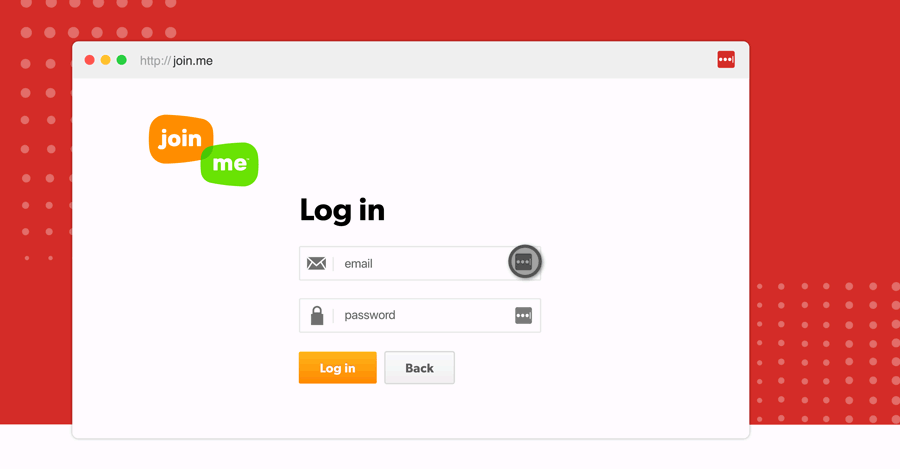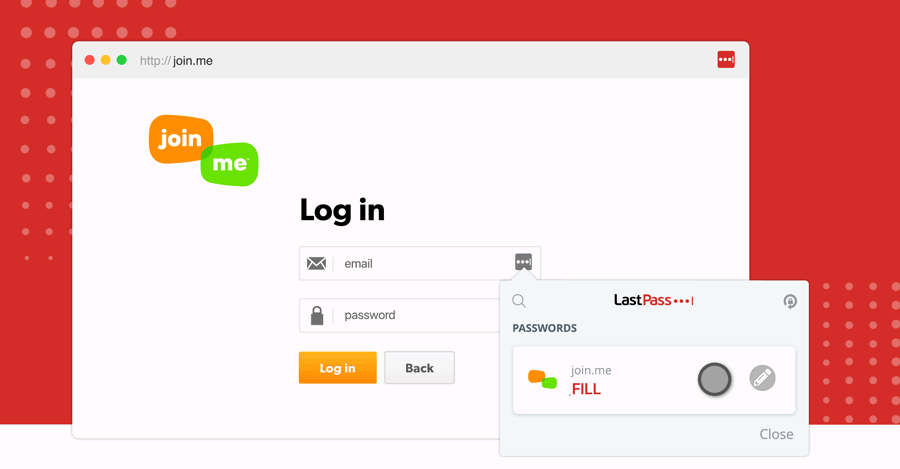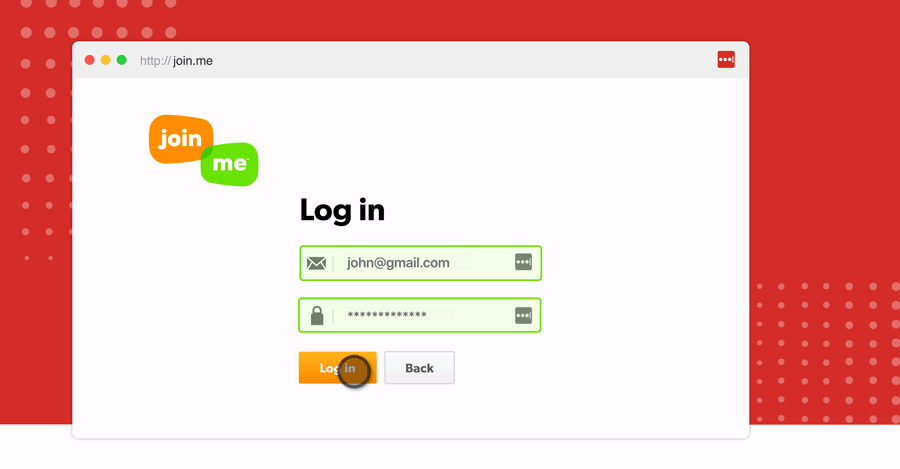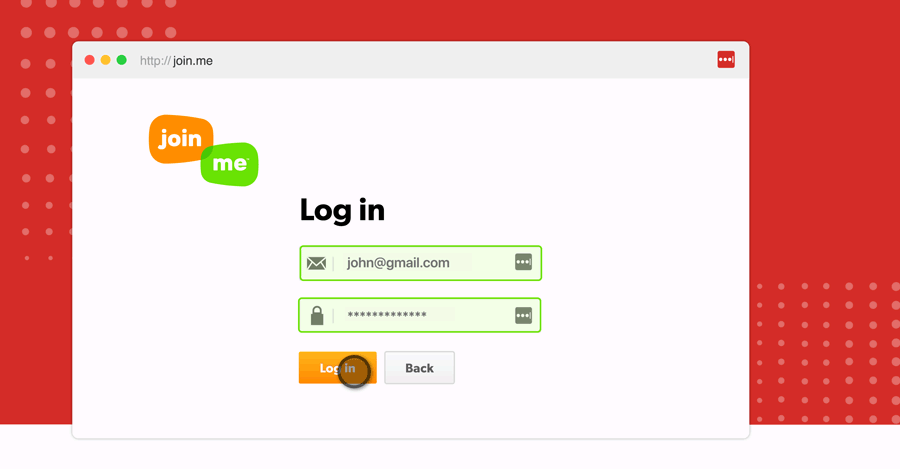
You and your business must understand the basic terminology around data breaches and hacks. Doing so can help you identify the warning signs of breaches, but it can also help you inform others of the risks to avoid. Moreover, businesses can use their knowledge to properly communicate with customers in a clear and timely method if a compromise ever occurs.
Understanding how hacks are discussed
Are you a consumer who’s unsure what a business is saying when notifying you of a past breach? Are you a business that wants to communicate with your customers if organizational data is compromised effectively?
It’s important to realize that these terms are regularly misused – where people will refer to security incidents as hacks. As a best practice, review the details you'll communicate to others, and always get your information from a reliable publication.
Tip: look to the company or organization involved first and foremost for statements, blogs, information, and more as your source of truth.